Whenever we speak to advertisers and agencies about app install fraud, we’re commonly asked the same set of questions. Not necessarily about the technical specifics, but the underlying human questions: who is committing this fraud, how do they do it, and why do it in the first place?
We’re here to answer those questions, one at a time, to help you understand where install fraud comes from. Starting with...
Who is committing app install fraud?
Although fraudulent app installs are a global problem for marketers, there is a notably higher proportion of bad players based in Russia, Israel and South-East Asia.
Fraudulent app install players take many guises. There are fraudulent suppliers who provide the tools for generating fake installs, whether it’s the technology for artificial installs or a human install farm, but in terms of who you are buying from, fraudulent players can be divided into two broad categories: publishers and ad networks.
Who are the fraudulent publishers?

Publishers – by which we mean media owners – can be completely fraudulent operations, running a portfolio of apps or sites whose sole purpose is generating money through fraudulent installs.
Typically, these apps are low-quality, but will have a presence in ad networks so they can access UA campaigns, and it can be hard to tell them apart from the other 4 million apps on the Google Play Store or 2 million on Apple’s App StoreAlternatively, it could be a publisher which generates some genuine installs but wants more money and intentionally boosts its revenue stream with fraudulent installs.
We’ve seen fraud coming from publishers who provide hundreds of good-quality installs. This can be a case of them actively employing a fraudulent player, or else acting in a way that will inevitably attract fraud – like posting their inventory on an offer wall.
Who are the fraudulent ad networks?
The ad networks we see install fraud from can be broken into three rough categories. The first are completely legitimate networks who are exposed to fraud without their knowledge – these produce an average of 12% fraudulent installs.
The most common type is negligent ad networks, who choose to turn a blind eye to the warning signs of fraudulent publishers. And then there are outright fraudulent ad networks, which are knowingly providing fraud.
In a recent report analysing all the installs Machine processed between January and May 2018, we saw that five of the 88 biggest networks used by our clients were delivering 100% fraudulent app installs. Unless these networks are highly incompetent, this can only mean that they’re deliberating providing fraudulent inventory.
These three types of ad network form a sort of chain. Fraudulent installs from the first, more innocent players show the fingerprints of the very worst offenders.
How is fraud generated?
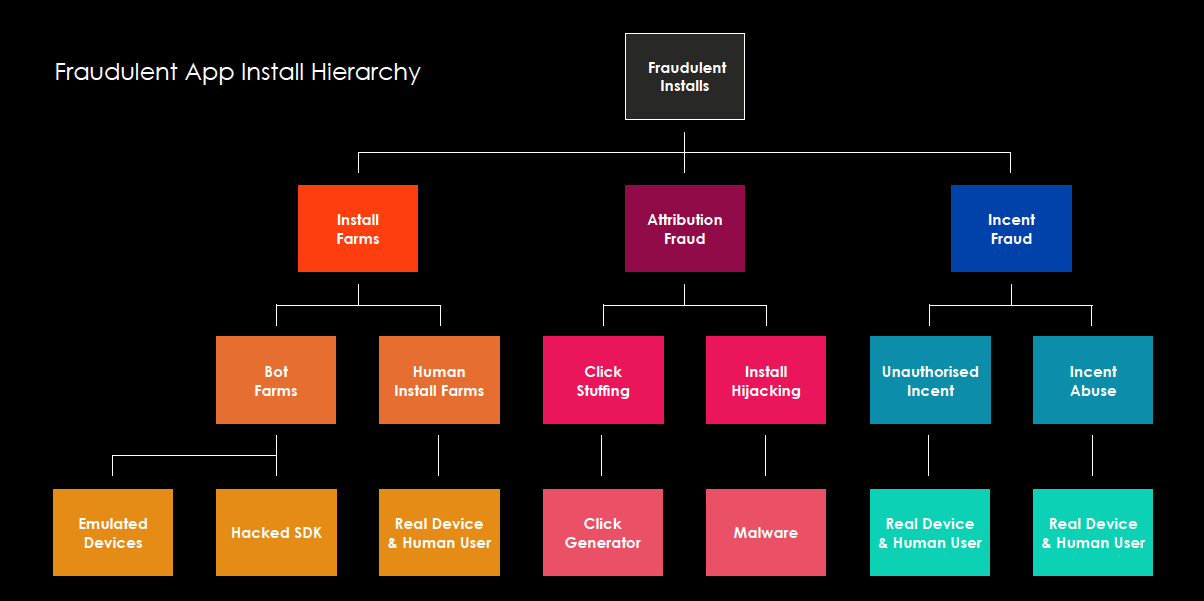
There are a wide variety of methods used to generate fraudulent installs, but you can broadly break it down into two categories: human and artificial.
Human-generated fraud can include people working in Install Farms, clicking ads on multiple devices in a row. It can also take the form of Unauthorised Incent, where installs are given to an incentivised publisher without the advertiser’s knowledge. It can even be on an individual level, as is the case with Incent Abuse – this is where a single person masks their location with a VPN and browses offer walls, downloading apps in exchange for monetary rewards, clearing out one country and then moving to the next.
On the artificial front, there are two types of attribution fraud: install hijacking – which uses a real app loaded with malware – and click stuffing. The latter is very easy to detect, as it generates millions of clicks, meaning it’s a telltale sign of a suspicious ad network or publisher.
There are also bot farms which use emulated devices – meaning dozens of virtual phones loaded onto a single computer – and the hacked SDK method, where an MMP’s SDK is reverse engineered to trigger events like installs, gameplay or even payments that never actually happened.
For more in-depth definitions of all these terms,
 .
.
How do my ad buys end up in the hands of fraudsters?
The digital ad industry has a small handful of genuine ad networks, with direct access to exclusive inventory, but a long tail – the majority of the market – who just rebroker advertisers’ offers over and over again. By doing this, they make fraud an inevitability.
We've already discussed the three types of fraudulent ad networks we see. As re-brokering continues, it passes from the first type – completely legitimate ad networks which simply haven’t taken enough precautions against fraud – to the more unscrupulous end of the spectrum.
The market repeatedly regurgitates the advertiser’s offer until it’s only attractive to fraudulent players. In some cases, we’ve seen clients paying $6 to the market, but it gets passed along the chain, gradually losing value, until it pops up on an offer wall for just 15 cents. And the only way you can make that kind of pricing work is by deploying fraudulent methods.
How do the fraudulent players get paid?
Whether the methods used are human or artificial, in almost all cases fraudsters need to
be connected to an ad network, in order to access the revenue that’s coming in, and get their money paid out.
Depending on the type of fraud, they can be paid directly by a publisher trying to boost its install numbers. Alternatively, they might run a portfolio of apps or sites and get paid by ad networks like any other publisher.
Why does app install fraud happen?
The answer to this question is relatively simple: money.
With Business Insider predicting that $6.7bn will be spent on app install ads this year, in the US alone, it’s big business for fraudsters. 53% of the app installs Machine analysed in H1 2018 were fraudulent – so just in the US, that’s $3.5bn annually going to fraudsters.
For an efficient fraudulent app install organisation, we’re talking about a potential gain in the tens or even hundreds of millions.
The other side of the equation here is the lack of penalisation for fraudsters. Compared to most other criminal activity, the ratio of risk to reward is massively disproportionate for app install fraud. To our knowledge, no one has ever been prosecuted over app install fraud.
With such huge potential rewards, little fear of being penalised and targets that have little to no protection, it’s no surprise that criminals find app marketing an appealing soft target. The vital thing is knowing how to stop them – and that’s where Machine comes in.
.jpg)

