In the first five months of this year, Machine has analysed over 22.4 million app installs, 56% of which we detected as fraudulent.
But where exactly are these 12.3 million fraudulent installs coming from? To find out, we analysed the 88 ad networks which delivered 500 app installs or more to our clients during this period.
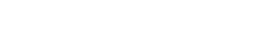
The graph above shows the percentage of installs from each ad network which were detected as fraudulent.
Of these 88 ad networks, only a single one delivered less than 10% fraudulent app installs. The rest fell somewhere between 15% and 100% fraudulent. Five of the networks delivered 100% fraudulent installs.
The list of 88 networks also includes the big two self-attribution platforms. One of these self-attribution platforms delivered over 30% fraudulent installs; the other, over 50%.
Finally, it’s worth noting that these aren’t all the ad networks we analysed – there’s also a long tail of over 160 networks which delivered under the 500-install mark. Some of these smaller networks were the very worst offenders, delivering 100% fraudulent installs – but as you can see from the above, it’s certainly not the case that working with larger players protects you from app install fraud.
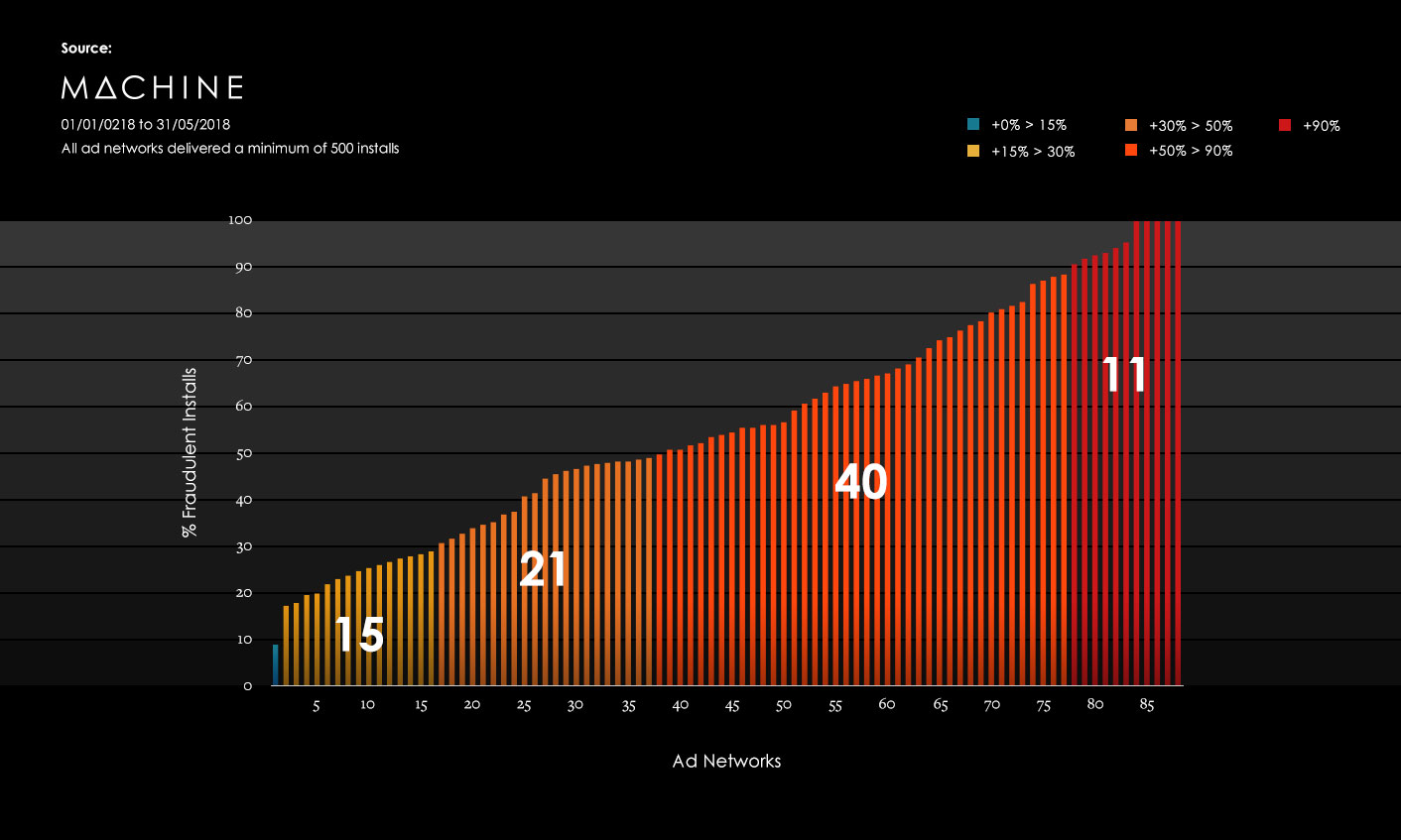
In this chart, we break down those 12.3m fraudulent installs by category, to establish which are the biggest problem areas for app install fraud.
All of these types of app fraud can be categorised into Human, and Non-Human app install fraud.
Human fraudulent app installs represent 38.4% of the total. These include Human install farms, Unauthorised incent, Incent abuse and mistargeted. Using the average CPI - of all our clients - Human app install fraud would have cost our clients approximately $10.6m, had they not been protected.
These human varieties include, incent fraud (21.3%)– illegitimate activity with incentivised app installs, can be broken down into unauthorised incent (12.6%) typically offering the user a in-game incentive to install apps, and incent abuse (8.7%) which are offer-walls paying real cash to the user - as well as human install farms (11.3%), which are physical locations with real people installing apps on real devices. The smallest category, mistargeted (5.8%) covers installs where the wrong app version has been downloaded or in the wrong geographical location – common signals of foul play.
Non-human fraudulent installs represent 61.6%. These include Install Hijacking, Hacked SDK, and Auto-bot farms. Machine saved our clients approximately $17m of lost revenue to non-human fraud.
The single largest category was install hijacking, which accounted for 32.3% of all fraudulent installs – nearly 4 million installs in total. Install hijacking is a form of attribution fraud which infects a user’s device with malware that monitors their activity and, whenever they download an app, fires a fake click at the corresponding MMP to gain credit for an organic install.
The fastest growing category is hacked SDK fraud (19.4%). Also known as SDK spoofing, this is an advanced form of fraud which involves exposing weaknesses in the MMP’s encryption, hacking their SDK to seemingly trigger events – like installs, payments or in-game events – which never actually happen, but which the client pays for nonetheless.
Other varieties include auto-bot farms (9.9%), a more sophisticated and efficient virtual version of human install farms which can be operated remotely from a computer.
It’s worth noting that, because these figures only cover fraud once the app install has happened, they do not include click analysis – meaning they exclude click stuffing, a type of attribution fraud which works by flooding an MMP with millions of clicks. Machine blocks artificial clicks, which reduces click stuffing to almost 0%. Click stuffing is detailed in the next pie chart.
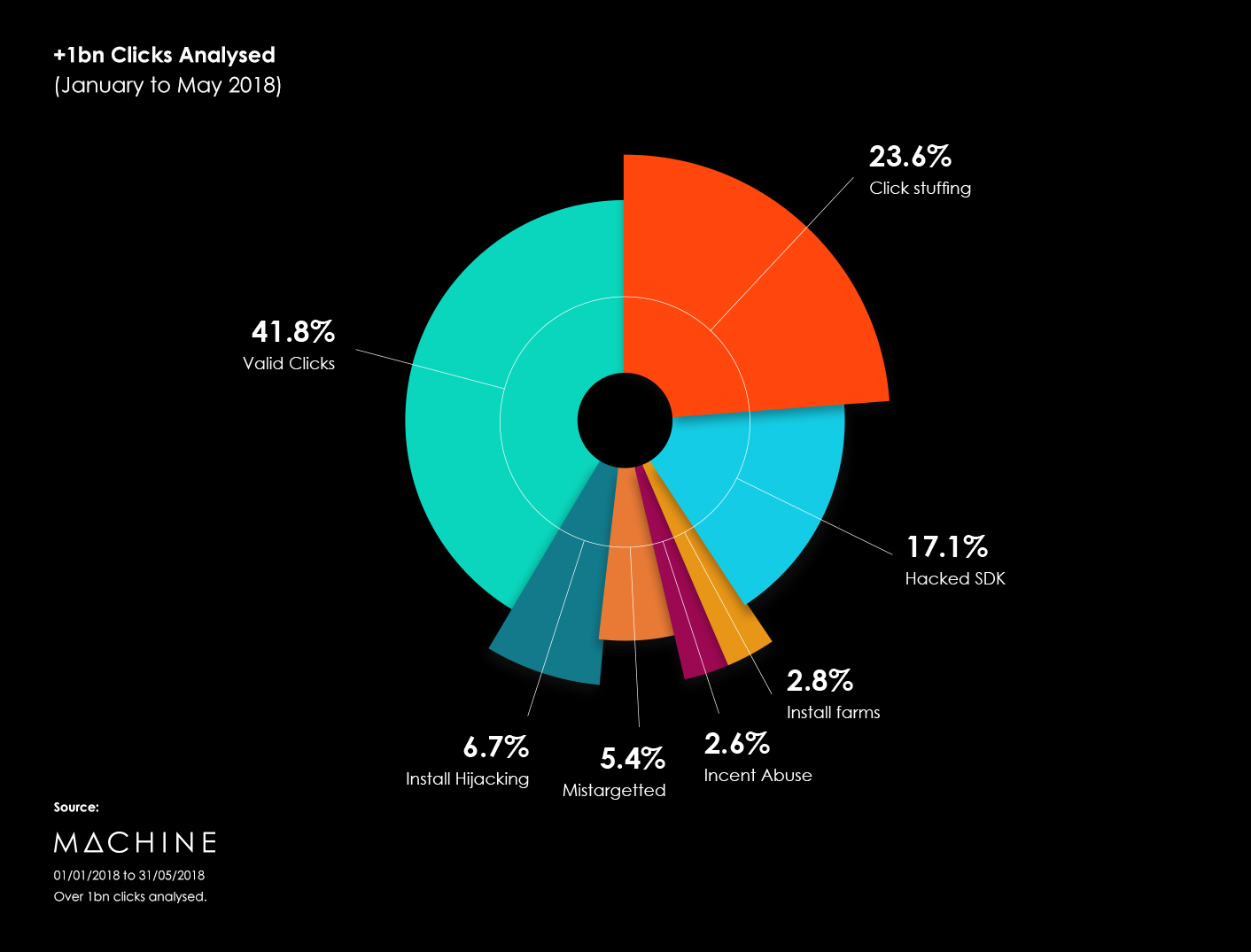
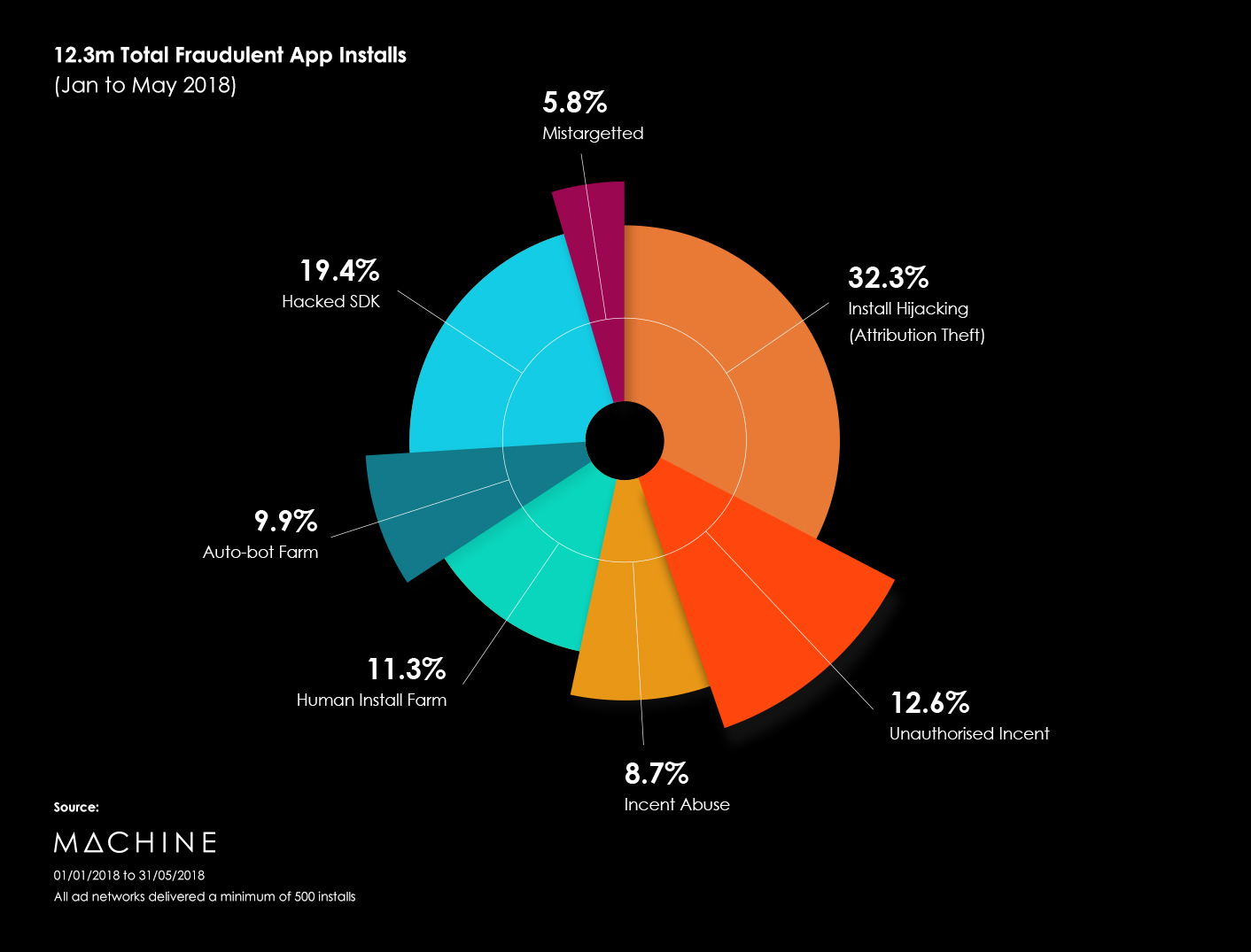
In the same period, Machine analysed over 1 billion clicks from 169 ad networks. 58% of these clicks Machine detected as fraudulent. In the chart above, we break down that fraud by category.
Of the 169 Ad Networks, 21 were 100% fraudulent. From these 21, 82% of the fraud came from Click stuffing, a form of attribution theft.
Click stuffing, fires thousands of fake clicks in close proximity at an advertiser’s MMP, increasing their chances of gaining the last click attribution and credit for an organic install. This accounted for 23.6% of all clicks which we analysed.
As a result of Machine preventing click stuffing, our client's organic installs increased by approximately 7.6 million.
As reported in the first pie chart, the fastest growing month-on-month – is hacked SDK fraud, which accounted for 17.1% of clicks.
There is light at the end of the tunnel
It's worth pointing out; it's not all negative. In the same period - utilising the same ad networks in this report - our clients acquired millions of real high performing app installs.
Most ad-networks are good players, who are affected by fraudulent app installs themselves. In today's market, any digital marketer worth their salt wouldn't dare run a desktop campaign without the protection of an ad verification tool such as IAS, Moat or Double Verify. If you're going to buy mobile app installs from ad-networks and social media, you need a specialist who can protect you against fraudulent app installs. Let us help.
To download a PDF version of this report

To understand more about each of these fraud tactics, please download the Machine glossary